
A CISO’s guide to cybersecurity in action

Fighting cybercrime with open-source SOAR tools

Cybersecurity Week in The Hague kicks off

The stakes are high in OpenAI’s shift to for-profit

CISO Platform Nederland, ECSO form partnership

Chinese botnet contains thousands of Dutch devices

RaaS and the commercialization of cybercrime

YubiKeys’ unfixable security flaw: Should you be worried?

Growing demand for cybersecurity specialists in the Netherlands

Need for cyber risk management greater than ever

“AI allows us to upskill our entire team”

“Threat actors are increasingly targeting OT organizations,” report

The three-point action plan for new CISOs

Quishing: an evolving threat
“NIS2 challenges us CISOs to concretize our work”

Achieving EU cyber compliance through a comprehensive application security strategy

What’s the cost of downtime?

“Wide-ranging fight against cybercrime due to global scale more important than ever”

Three areas where CISOs can augment their cybersecurity approach

CISODAY in the rear view

CISODAY aftermovie

KPMG Cybersecurity Considerations 2024

“Building collaboration in the Dutch security ecosystem is key to protecting our country”

Jeroen Schipper is CISO of the Year 2024

CISO of the Year Award special with Floor van Eijk

CISO of the Year Award special with Jan Joost Bierhoff

CISO of the Year Award special with Jeroen Schipper

CISO of the Year Award special with Lies de Wit

CISO of the Year Award special with Pieter van Houten

“The CISO is no longer just a necessary evil”

“Become the enabler, not the blocker”

Zero Trust: how do I make it concrete?

Are you ready for NIS2?

CIOs and CISOs: managing tensions and working together effectively

Offensive cyber ops continue to increase, MIVD calls for adequate mandate, legal revisions

“Government action against ransomware necessary”

Open-source software supply chain attacks are on the rise – but they’re mainly our own fault

One third Dutch companies susceptible to data breaches due to poor compliance

Eight cybersecurity predictions for this year (and beyond)

A cyber-samurai in the digital dojo…

The Great Reset – Why we haven’t yet seen the end of the Big Tech layoffs

Two thirds of employees gamble with security

Government launches NIS2 Quick Scan

The AVG and IB

Hackers are friends, not food – how they can help you

CISO Platform Nederland board is complete

ZBO without embargo

The C in CISO stands for Compliance

A CISO’s guide to cybersecurity in action
Put cyber security into action. Discover practical recommendations for top-tier technologies and tools that can augment and elevate your security initiatives as a CISO. Unlock power and potential. Explore these solutions: AI-powered threat intelligence, zero trust, a consolidated cyber security architecture and unified cloud-native security.

Fighting cybercrime with open-source SOAR tools
To combat the challenges around the existing SOAR tools and help organizations improve their cybersecurity posture, TNO has launched an open-source SOAR tool.

Cybersecurity Week in The Hague kicks off
From September 30 to October 4, The Hague’s Cybersecurity Week 2024 will bring together experts, companies and international delegations to share knowledge, collaborate, promote innovation, increase cyber awareness and strengthen cybersecurity solutions.

The stakes are high in OpenAI’s shift to for-profit
OpenAI’s reported move to a for-profit organization might push Sam Altman’s plans for more data centers and nuclear energy forward, but it will come at a cost, the tech world worries, leaving no space for OpenAI’s initial top priority: keeping humanity safe.

CISO Platform Nederland, ECSO form partnership
This week, CISO Platform Nederland, the Dutch platform for Chief Information Security Officers (CISOs) and other high-ranking cybersecurity professionals in medium and large enterprises and non-profit organizations, has formalized its collaboration with the CISO Community of the European Cyber Security Organisation (ECSO).

Chinese botnet contains thousands of Dutch devices
Cyber actors linked to China have compromised over 260,000 devices with the goal of creating a botnet, the FBI reported this week. Of those devices, thousands are located in the Netherlands.

RaaS and the commercialization of cybercrime
As we get better at defending, criminals also get better at attacking. They do so by professionalizing their services, almost working similarly to legitimate software businesses, and creating a business model of attacks: selling Ransomware-as-a-Service (RaaS).

YubiKeys’ unfixable security flaw: Should you be worried?
Security researchers have detected a vulnerability in YubiKey two-factor authentication tokens that enables attackers to clone the device, its manufacturer Yubico announced this week.

Growing demand for cybersecurity specialists in the Netherlands
In many countries, the demand for cybersecurity professionals is decreasing. But in the Netherlands, organizations are actually looking more intensely for them. The number of vacancies for cybersecurity roles on LinkedIn has increased by more than two percent in the country over the past year. This is indicated by research from LinkedIn.

Need for cyber risk management greater than ever
Organizations are increasingly dependent on technology to execute their business processes and deliver products and services. Cybersecurity incidents disrupt these business processes, which can have a major impact on organizations. As a result, cyber risk has emerged as a top agenda point with more and more board-level attention worldwide.

“AI allows us to upskill our entire team”
By implementing AI and automation tools in the right way, a significant opportunity arises to drive career growth in security teams, according to Ian Stacey, Group Head of Information Security at Novuna and Callum Taylor, Cybersecurity Product Owner at Novuna.

“Threat actors are increasingly targeting OT organizations,” report
OT organizations are making progress in hardening their security, but their cyber teams still face significant challenges in securing converged IT/OT environments. Adopting essential tools and capabilities to enhance visibility and protections across the entire network will be vital for these organizations when it comes to reducing the mean time to detection and response.

The three-point action plan for new CISOs
Unlock the essential strategies for new CISOs to enhance asset visibility, manage vulnerabilities, and ensure regulatory compliance with Hadrian’s comprehensive “Three-Point Action Plan” eBook.

Quishing: an evolving threat
The ongoing changes in QR code phishing, or quishing, show us that it is important to be observant and to not heavily rely on our email security systems.
“NIS2 challenges us CISOs to concretize our work”
By making security concrete and tangible, the implementation of NIS2 will create more understanding for the role of CISO, says Justin Broeders, concern-level CISO at the Ministry of Finance.

Achieving EU cyber compliance through a comprehensive application security strategy
A glance into how upcoming EU cyber legislative requirements prescribe enhanced approaches to the resilience of digital solutions and its properties with robust supply chain risk management efforts – steering the future of software security and compliance practices.

What’s the cost of downtime?
What happens when a large organization faces DDoS attacks, software failures, or even a company-wide hack? While the direct costs of unplanned downtime are easily visible, organizations should not underestimate the indirect, or hidden costs of digital failures.

“Wide-ranging fight against cybercrime due to global scale more important than ever”
Last year, 2.3 million Dutch people were affected by a form of online crime, which is associated with huge financial losses, but above all affects trust in each other and in the digital infrastructure, according to the Cybercrime Assessment Netherlands 2024 by the OM and the Police.

Three areas where CISOs can augment their cybersecurity approach
CISOs who elevate response and recovery to equal status with prevention are generating more value than those who adhere to outdated zero-tolerance-for-failure mindsets, according to analysts from Gartner.

CISODAY in the rear view
In a packed Green Village, about 200 security experts got together to celebrate the very first CISODAY.

CISODAY aftermovie
Missed CISODAY? Get a quick impression so you get the picture!

KPMG Cybersecurity Considerations 2024
In our annual considerations report, KPMG cybersecurity specialists explore eight considerations to take into account for 2024.

“Building collaboration in the Dutch security ecosystem is key to protecting our country”
As CISOs, we have a responsibility to drive collaboration and technological innovation within the Netherlands, says Mahdi Abdulrazak, Group Information Security and Risk Officer at SHV Energy, a leading global distributor of off-grid energy.

Jeroen Schipper is CISO of the Year 2024
Jeroen Schipper, CISO at the Municipality of The Hague, won the CISO of the Year 2024 Award last night. He owes the award to his transformational role and his holistic and inclusive approach to cybersecurity. His contributions to the professionalization of the CISO profession and his role as an active representative of the city of The Hague in cybersecurity matters were also taken into consideration.

CISO of the Year Award special with Floor van Eijk
In this last episode, we talk to Floor van Eijk, CISO at NN Group, and nominated for the CISO of the Year Award 2024. Other guests are jury member Job Voorhoeve (Amrop) and CISODAY partners Boudewijn van Lith (Proofpoint) and Thijs Timmerman (KPMG).

CISO of the Year Award special with Jan Joost Bierhoff
In this episode, we talk to Jan Joost Bierhoff, Global CISO at Heineken, and nominated for the CISO of the Year Award 2024. Other guests are jury member Madelein van der Hout (Forrester) and CISODAY partners Marijn van Overveld (Noesis) and Daan Hakkert (IBM).

CISO of the Year Award special with Jeroen Schipper
In this episode, we talk to Jeroen Schipper, CISO at Gemeente Den Haag, and nominated for the CISO of the Year Award 2024. Other guests are jury member Madelein van der Hout (Forrester) and CISODAY partners Vincent van Kooten (Netskope) and Mark van Leeuwen (Okta).

CISO of the Year Award special with Lies de Wit
In this episode, we talk to Lies de Wit, CISO at Stater, and nominated for the CISO of the Year Award 2024. Other guests are jury member Job Voorhoeve (Amrop) and CISODAY partners Ivo van Bennekom (PwC) and Hans van den Boomen (CheckPoint).

CISO of the Year Award special with Pieter van Houten
In this first episode, we talk to Pieter van Houten, CISO at SHV, and nominated for the CISO of the Year Award 2024. Other guests are jury member Madelin van der Hout (Forrester) and CISODAY partners Mike Remmerswaal (Netskope) and Mark van Leeuwen (Okta). The host is Rob Beijleveld.

“The CISO is no longer just a necessary evil”
Last month, during Amrop’s Global Digital Practice Quarterly Online Event "The evolution of the CISO role: CISO as a business enabler" we heard from and spoke to Harvey Ewing, CISO turned CIO, who is now again a CISO at Radial Inc., and to Dimitri van Zantvliet, CIO...

“Become the enabler, not the blocker”
A great CISO is one who can embrace innovation and new business goals, but at the same time, knows how to create awareness about security risks, says Luisella ten Pierik, CISO of regional grid operator for electricity and gas Stedin and manager of their CIO Office.

Zero Trust: how do I make it concrete?
Every year, numerous research and consultancy firms come up with all kinds of overviews of strategic trends in IT and cybersecurity. Invariably, Zero Trust is part of these lists, with definitions along the lines of “don’t just trust anything, but verify”. But how exactly should you go about this as a CIO, CISO, or IT manager?

Are you ready for NIS2?
Although the Dutch legislation for NIS2 is running behind, the Dutch business sector should start getting their things in order, especially if they are dependent on international customers and suppliers.

CIOs and CISOs: managing tensions and working together effectively
CIOs and CISOs on the pros and cons they see in the CISO reporting to the CIO vs. working as peers, ways of effectively addressing the tension, and the governance standards needed for cybersecurity framework to align with organizational goals and industry security requirements.

Offensive cyber ops continue to increase, MIVD calls for adequate mandate, legal revisions
The Netherlands remains an important target for Russian cyberoperations, and threats are only increasing, the Dutch Military Intelligence and Security Service (MIVD) mentioned in its yearly report. The Service calls for an adequate mandate so it can effectively carry out the necessary investigations against these offensive cyber programs.

“Government action against ransomware necessary”
The government should actively support the business community in the fight against cybercrime through targeted measures such as investment deductions and reduced VAT rates for security services.

Open-source software supply chain attacks are on the rise – but they’re mainly our own fault
The recently discovered XZ Utils backdoor has highlighted the vulnerabilities in open-source software. However, although open-source software supply chain attacks have tripled since 2019, most of them are easily preventable.

One third Dutch companies susceptible to data breaches due to poor compliance
More than a third of all Dutch companies failed a compliance audit in the past 12 months. As a result, they are ten times more likely to suffer a data breach. Ten percent of Duch companies became victim of a ransomware attack. Of all those, four percent paid a ransom.

Eight cybersecurity predictions for this year (and beyond)
In March, Gartner revealed its cybersecurity predictions for 2024 and beyond. Its analysts believe generative AI (GenAI) adoption will close the cybersecurity skills gap and reduce employee-driven cybersecurity incidents. They also predict that two-thirds of global 100 organizations will extend directors and officers insurance to cybersecurity leaders due to personal legal exposure.

A cyber-samurai in the digital dojo…
In the serene yet potent ethos of ancient Japan, where the discipline of Budo, the martial way, was not merely about combat but a profound journey towards self-mastery, integrity, and the protection of one’s community, we find surprising parallels to the modern role of a CISO in the realm of critical infrastructure.

The Great Reset – Why we haven’t yet seen the end of the Big Tech layoffs
After seeing two years of post-pandemic economic downturn and massive layoffs in the tech sector, recovery seemed to be on the radar for 2024. However, jobs continue to be impacted. But in the cybersecurity industry the shift to AI and low interest rates, that facilitate finding capital, have led to an increase in hiring.

Two thirds of employees gamble with security
Over two-thirds of Dutch employees knowingly put the organization at risk, leading to ransomware or malware infections, data breaches or financial loss. More than four in five of the organizations surveyed experienced at least one successful attack by 2023.

Government launches NIS2 Quick Scan
On February 29, the central government launched the NIS2 Quick Scan that allows organizations to prepare for the new European NIS2 directive. This directive is aimed at increasing the digital resilience of companies and organizations in the EU.

The AVG and IB
You frequently see the CISO/Privacy Officer roles combined. I did combine it myself for a while. Even though the two topics overlap, they are also very different. Because the interests (data subjects vs. organization) are apart and also the scope differs from each...

Hackers are friends, not food – how they can help you
Hackers are invaluable to your organization. They have the time and motivation to fiddle endlessly with a thread until an entire sweater is reduced to a pile of yarn. Whereas pen testers have limited time and are paid by the hour, reporters at a CVD often charge nothing at all. All they want is a T-shirt and an honorable mention. How do you get them to work for you?

CISO Platform Nederland board is complete
The board of CISO Platform Nederland, the non-profit association of CISO community Nederland, is complete: CISOs Dimitri van Zantvliet, Luisella ten Pierik, Mahdi Abdulrazak, Justin Broeders and co-founder Rob Beijleveld officially joined the organization’s board on February 16.

ZBO without embargo
Originally a talk I gave at a lunch meeting with several ZBOs. ZBO stands for independent administrative body. These are the government agencies that have independent governance but belong to a ministry. That this is a complex construction, you will already...

The C in CISO stands for Compliance
''We are ISO certified and therefore 100% cyber-secure!'' A statement that I think few security experts will endorse. And yet, compliance is an important and sometimes useful tool within information security. With the current laws and regulations, you can't really...

Monitoring for dumbasses – the importance of logging and monitoring
Logging and monitoring. A golden duo. But what exactly is that - logging? And how do you do it properly? I hear a lot of talk about the ''next gen'' solutions like XDR and the ''SIEM is dead.'' But is that really true? If most organizations don't even have their...

Dutch government fails to meet implementation of NIS2 and CES on time
Businesses are not the only parties experiencing problems with implementing of the new European guidelines for Network and Information Security (NIS2) and the Critical Entity Resilience Directive (CER). In the Netherlands, the preparations for the consultation on the Dutch implementation of these European directives are already delayed.

Your vote, your voice?
Attempts to meddle in election processes through cyberattacks have increased drastically, and the methods with which hostile actors try to infiltrate society are continually evolving. Cybersecurity professionals have a role to play in this trend by educating the general public about these risks so that more stakeholders can act as a defense against hostile state actors.

Learning to advise
''Gives solicited and unsolicited advice'' is often in our job description. Giving advice is a skill. One which is relevant to a range of roles within information security. For (C)ISOs as well as consultants and pentesters. But how do you give good advice? What is the...

Security vs. privacy
Security and privacy are two topics hardly mentioned in one breath in daily security operations. On the one hand, this is a good thing because when tactical and strategic thought is given to safeguarding privacy within security, the operation can run freely within those set frameworks.

Airbags and aliens – performing risk analysis without stress!
A quality risk analysis is one that you, the expert, stand behind. You must be able to explain and defend the outcome. Risk analyses are used to identify risks, determine measures and put responsibility where it belongs. But after the report you (C)ISO are not...

Ten security myths debunked (podcast)
“Public WIFI is unsafe,” and “Password books are a bad idea!”. CISO Fleur van Leusden debunks these myths and eight more. This podcast is in Dutch.

2024: you better take it personally!
Welcome to 2024, a year where the cyber landscape isn’t just evolving; it’s demanding a revolution in how we think and act. The message for you is unequivocal: It’s time to take it personally.

A hacker’s wishlist for Christmas
Every year, cyberattacks increase dramatically during the holiday season. Criminals know how to take advantage of a busy season in which companies endure chaos and employees are busy, stressed, tired, and ready for a break.

“This is your CEO calling. Can you pay this invoice for me?”
In many companies, artificial intelligence is slowly getting ingrained in work processes. Generative AI tools such as ChatGPT make it easy to replace time-costly processes such as generating summaries, creating marketing content, and automating customer service.
Yet, AI evolves at high speed, and the business sector needs to wake up. Looking at the biggest cyber security trends in 2024 that everyone must prepare for, generative AI is on top of the list, according to Forbes. Cybercriminals are increasingly incorporating AI in their attacks, ranging from deepfake social engineering attempts to automated malware.

CISO community, CISO Platform Nederland established officially
The CISO community Nederland and the associated CISO Platform Nederland are a reality. The new combination supports Dutch companies’ Chief Information Security Officers (CISOs) in various industries, non-profit organizations, and the government.

“Watch your back” or “I’ve got your back”?
Chief Information Security Officer – sounds great, but is it? It sounds like an amazing position if all goes well… But what if your organization suffers from a large-scale cyber incident? Unlike other C-level positions, things may have personal consequences rather quickly for the CISO, mainly due to the enormous risk and impact of cybersecurity incidents. “You would take care of it, right?” “How could we have been hacked?” “I thought we had a good CISO?!” Unfortunately, judgments are made in split seconds.

Fighting cybercrime in a more targeted way with “Melissa”
On October 3, the “Melissa” covenant was signed by The Public Prosecution Service (OM), the police, the NCSC, Cyberveilig Nederland, and ten private parties. In this partnership, the groups join forces to fight cybercrime in a more targeted way, to increase the chances of catching cybercriminals, and to reduce the chance of impact for victims.

The threat landscape evolves: CISOs need to advocate for better cyberresilience
While the threat landscape is continuously evolving, our attack surface is growing too, says Dimitri van Zantvliet, Director Cybersecurity & CISO at NS and one of the initiators of the CISO community. CISOs have a vital role in convincing boards to act now. In...

Moving toward a decentralized digital identity – what’s changing?
In the next few years, the EU expects 80% of citizens to use digital identity for public services. While moving to a decentralized digital identity framework will provide opportunities for every industry, companies must anticipate the changes.

“CISOs should have a prominent place on the board – and beyond”
The CISO will be an important stakeholder in the coming years, according to Rob Beijleveld, one of the initiators of the CISO community. CISOs have to take steps to develop their role, increase cybersecurity awareness, advocate for changes, and show that they deserve that seat at the table.

‘Guy Fawkes’ and the digital rebellion
The mask featuring the mug of Guy Fawkes – a figure from the English seventeenth century – with its iconic white face, subtle smile, mustache, and pointed beard has experienced an unexpected renaissance in recent decades.

CSBN 2023: Digital threat to the Netherlands undiminished
Every organization must be prepared for unexpected attacks, warns the National Coordinator for Counterterrorism and Security (NCTV), who published the Cybersecurity Assessment of the Netherlands (CSBN) 2023 early this month. The CSBN reflects the trends, incidents, threats, and challenges in cybersecurity within our national security.
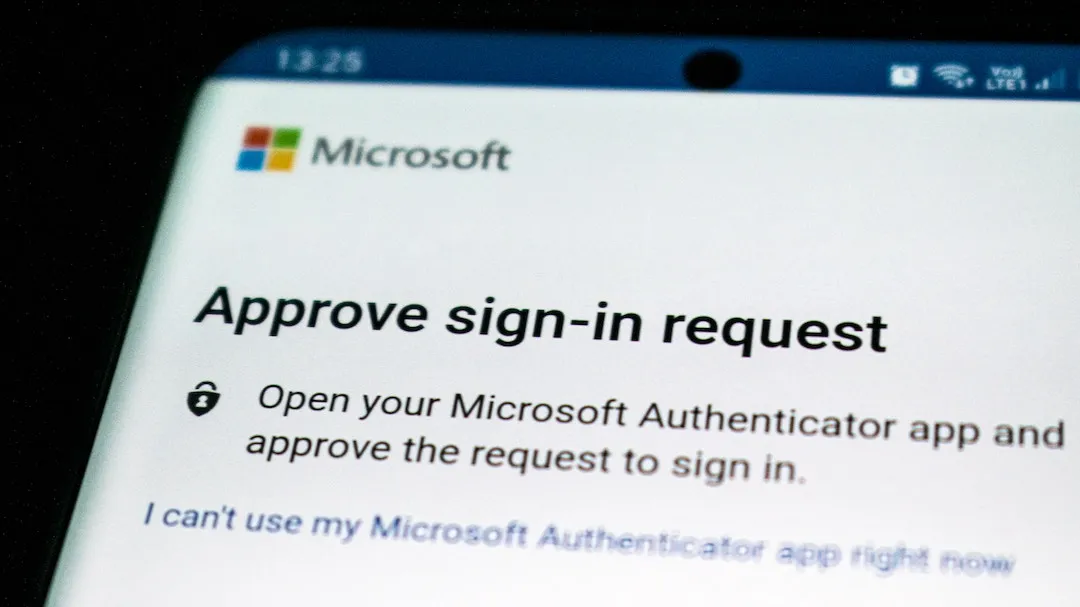
Sharp increase in attacks on decision makers’ cloud accounts
The number of successful cyberattacks taking over the cloud accounts of top executives has increased by more than 100 percent. Cybercriminals are using a phishing tool – EvilProxy – based on a reverse proxy that they use to steal MFA data and session cookies, according to research by Proofpoint.

Organizations fend off 6 out of 10 attacks
Security teams make four “impossible” trade-offs when fending off threats. They must decide which attacks to prioritize; choose which vulnerabilities to fix; optimize prevention or detection controls; and finally decide what to log and what to warn about. So reports Picus Security following a report released this month.

Government decides on one organization for cybersecurity
The Cabinet has decided to merge the existing cybersecurity organizations of the central government. The National Cyber Security Center (NCSC) of the Ministry of JenV, the Digital Trust Center (DTC), and the Computer Security Incident Response Team for Digital Service Providers (CSIRT-DSP), both of the Ministry of EZK, will merge into a new organization.

An administrative view of cybersecurity at Dutch Railways
Cyber threats can occur at Dutch Railways (Nederlandse Spoorwegen or NS) in various places: trains, stations, workplaces, data centers, websites, mobile apps, and the chain. The key, according to CISO Dimitri van Zantvliet, is mapping the risks and responding to the threat landscape.

