In today’s digital era, organizations are increasingly dependent on technology to execute their business processes and deliver products and services. Cybersecurity incidents disrupt these business processes, which can have a major impact on the organization as well as its clients and business partners. As a result, cyber risk has emerged as a top agenda point with more and more board-level attention worldwide.
Most organizations do not have the required resources to implement the most advanced cybersecurity controls in all areas. Their key challenge is to ensure that the available resources are allocated towards cybersecurity controls that address their most critical risks. This implies that cybersecurity controls should be prioritized based on their value in terms of the magnitude of risk that they mitigate. This prioritization allows organizations to significantly increase the efficiency and effectiveness of their cybersecurity organization and protect the organization’s assets against its highest risks.
Cyber risk management provides a methodology to generate valuable insights into the cyber risk exposure of the organization. The key to an effective cyber risk management capability is setting up a continuous cycle to identify, assess, treat, and report on the organization’s key cyber risks.
Regulators worldwide are recognizing the need for cyber risk management. New regulations, such as the NIS2 Directive, demand that organizations implement cyber risk management capabilities. The NIS2 Directive specifically requires organizations to adopt measures that are commensurate with their cyber risk exposure, considering the potential impact of a cybersecurity incident on society and the economy. In this context, cyber risk management is a strategic necessity and an enabler for regulatory compliance.
Key elements of cyber risk management
Cyber risk management is a continuous cycle of identifying, assessing, treating, and reporting on cyber risks. Figure 1 highlights the key elements of this cycle.
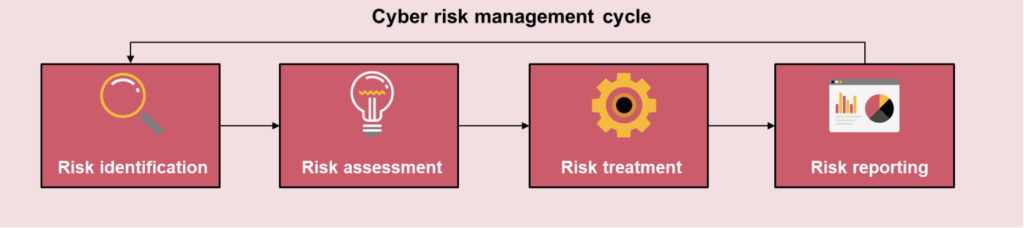
Figure 1: The cyber risk management cycle
Risk identification is the basis of the cyber risk management cycle and involves defining the organization’s key cyber risks. The main challenges for most organizations are setting up a clear definition of cyber risk that is understood throughout the organization and ensuring that all relevant factors (e.g. business context, threat actor profile, critical assets, threat model) are reflected in the organization’s cyber risks.
Risk assessment is the practice of evaluating the organization’s exposure to the identified cyber risks. Risk exposure is commonly expressed in terms of likelihood and impact, whereby the impact is often assessed along the lines of various impact areas (e.g. financial, operational, reputational). For NIS2 compliance, it is crucial to include an outside-in perspective in cyber risk assessments by evaluating the impact of cyber risks on society and the economy.
Risk treatment entails deciding upon the risk management strategy (mitigate, accept, transfer, and avoid) for each cyber risk based on the outcomes of the assessment. The key in this decision-making process is clearly defining the amount of risk that the organization is willing to accept, and the risk appetite.
Risk reporting is the process of continuously monitoring and reporting on the organization’s risk exposure and the effectiveness of controls toward stakeholders throughout the organization. In risk reporting, it is crucial to ensure that reports are tailored to the information needs of specific stakeholder groups (e.g. executive management, management teams, operational teams) and drive decision-making.
Transition towards Data-Driven Cyber Risk Management (DDCRM)
Setting up a basic cyber risk management cycle allows organizations to take the first step towards an efficient cybersecurity organization. For organizations that are more advanced in cyber risk management, the next step is to harness the power of data, allowing them to make more effective and reliable decisions based on various data sources and provide a higher level of transparency into their cyber risk exposure.
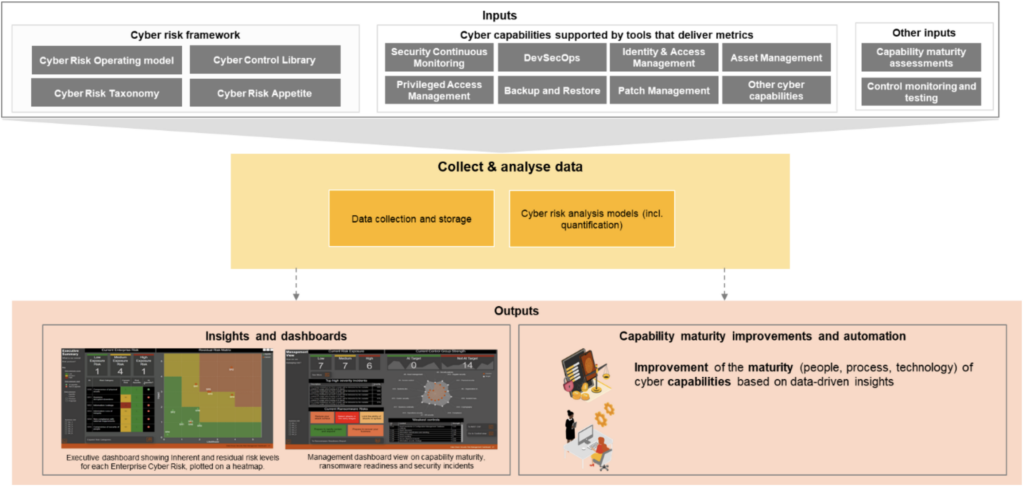
Figure 2: The building blocks of a DDCRM capability
In the current age of digitization, organizations possess an increasing amount of data that provides valuable insights into their cyber risk posture, threat landscape, and strength of cybersecurity controls. DDCRM is the practice of leveraging this data in the various steps in the cyber risk management cycle by linking data from various sources to the organization’s key cyber risks, threats, and controls.
The foundation of a DDCRM capability is a cyber risk framework. A cyber risk framework defines the organization’s approach to cyber risk management. It includes setting up a cyber risk taxonomy that defines the organization’s strategic cyber risks and the capabilities and controls that the organization has in place to mitigate these risks towards its risk appetite. The capabilities and controls should be based on the risks that the organization faces and take any specific requirements from cyber regulations and industry standards into account. In this way, the implementation of controls contributes to risk mitigation and enables compliance with cyber regulations.
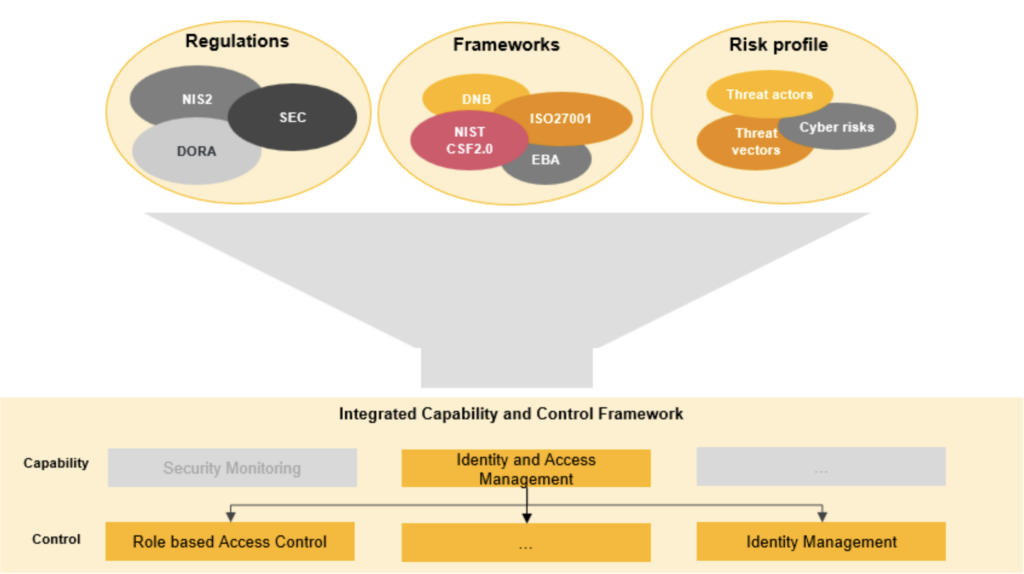
Figure 3: An integrated capability and control framework enables risk mitigation and regulatory compliance
Various data sources can provide valuable insights into the organization’s cyber risks, threats, capabilities, and controls. Various cybersecurity capabilities (e.g. Identity Management) are supported by tooling that provides valuable insights into the strength of cybersecurity controls. Other cyber risk management activities, such as capability maturity assessments and control monitoring and testing, also provide valuable input to provide insight into the risk posture of the organization.
The input data is collected and stored to provide input for cyber risk analysis models. Cyber risk analysis models generate insights into the cyber risk exposure of the organization based on data points on its threat landscape, controls, and other elements in the cyber risk framework. The output can be either qualitative or quantitative. For many organizations, the collection of cyber risk data requires significant manual effort. In their transition towards DDCRM, they are moving towards automated data collection (e.g. APIs) and storing data in a centralized cyber data lake.
The output of the cyber risk analysis models is used to create interactive and dynamic dashboards that cater to the needs of various stakeholder groups (e.g. executive management, security leadership operational IT, and security teams) within the organization. It is key that the information presented on these dashboards is in line with the reporting needs of the audience and drives decision-making, for example by highlighting concrete actions or decisions based on the information. In addition, the analysis models can automate (operational) cyber risk management tasks, such as automated analysis of vulnerabilities in systems or alerts generated by security monitoring tooling.
The journey towards DDCRM
One of the key challenges for starting the journey towards DDCRM is creating sufficient awareness of its benefits and delivering value to the organization within a short time frame. Organisations that successfully implement DDCRM take an incremental approach They start their journey by building a Minimum Viable Product (MVP) and gradually increase the level of data-driven input that is used within their cyber risk management processes.
Figure 4 highlights an example maturity journey for an organization to move from a traditional cyber risk management approach based on professional judgment towards DDCRM. The journey consists of the following phases:
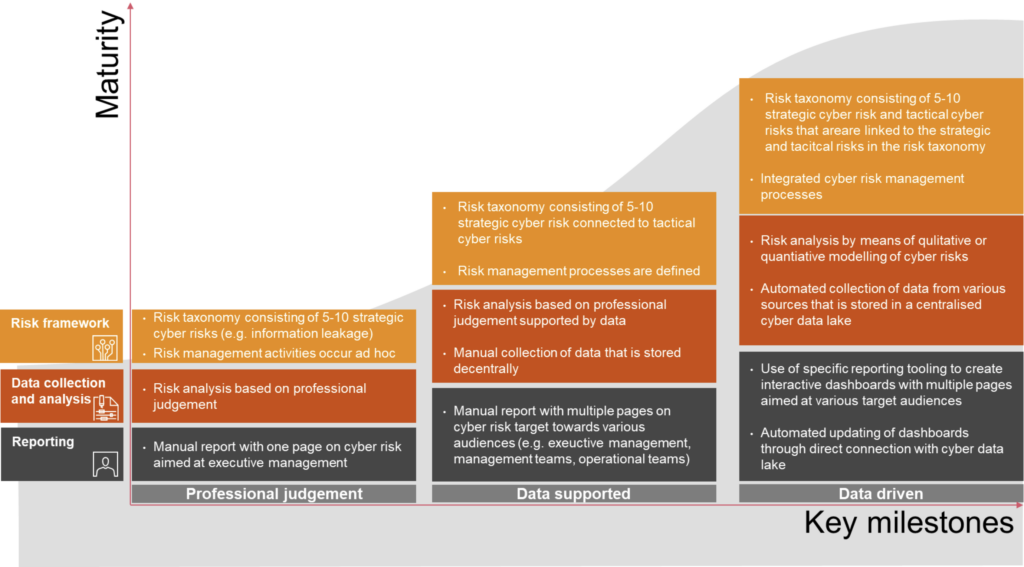
Figure 4: Example of maturity journey toward DDCRM
- Phase 1: Professional judgment – In the first phase, the organization defines a simple risk framework consisting of 5-10 strategic cyber risks and assesses the likelihood and impact of these risks based on professional judgment with a manual report as an output.
- Phase 2: Data supported – In phase two, the organization grows further by enhancing the risk framework with tactical cyber risks and defining cyber risk management processes. The assessment of the risks in the framework is supported by various data points (e.g. metrics) that are collected manually and reported in a manual report with various perspectives on cyber risk.
- Phase 3: Data-driven – In the final phase, the organization integrates strategic, tactical, and operational cyber risk management activities and implements risk models to assess its level of cyber risk. The required data to feed these models is collected automatically and stored in a centralized cyber data lake. The outcomes are reported through interactive live dashboards that are created with specialized dashboarding tooling.
By evaluating their position on this journey and determining the required next steps, organizations can move forward towards an efficient and transparent security organization that prioritizes their resources on their most critical risks and complies with cyber regulations.
By Nick Ho-Sam-Sooi, Luit Verschuur, Dilan Cosgun, Jan Visser, Suzie Bernards, and Peter Avamale



