
Growing attacks, genAI lead to heightened anxiety among CISOs, report
[Members only] The surge in cyberattacks is fueling heightened anxiety among CISOs. The rapid rise of generative AI is forcing security leaders to strike a balance between innovation and risk, according to

CISO: Secure the Future
In this podcast, Dave Maasland talks to none other than Richard Marko, CEO of ESET. From the heart of Europe, he shares how ESET has been working on digital autonomy since day one – long before it became a bu

Florence Mottay is CISO of the Year 2025
Florence Mottay, CISO at Zalando, won the Dutch CISO of the Year Award on CISODAY, which was celebrated on May 27, 2025.
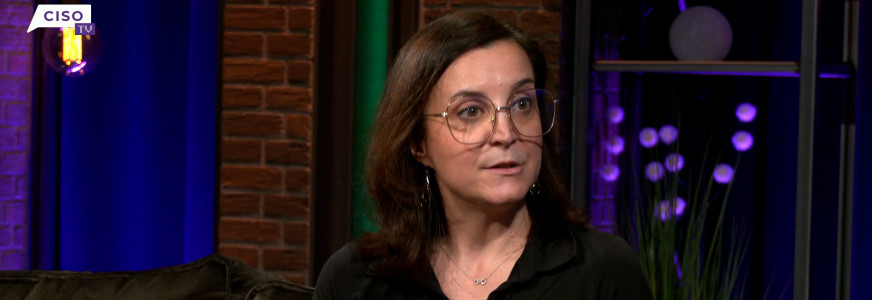
CISO of the Year Award special with Florence Mottay
In this episode, we talk to Florence Mottay, CISO at Zalando, and nominated for the 2025 CISO of the Year Award.

Florence Mottay: "CISOs are going to have to wear many hats"
Having started as an ethical hacker 25 years ago, Florence Mottay worked in several business roles and eventually became CISO at Zalando in 2022. She was recently nominated for the 2025 CISO of the Year Award.

CISO of the Year Award special with Vladimir Cibic
In this episode, we talk to 2025 CISO of the Year Nominee Vladimir Cibic, CISO at KPN.

Vladimir Cibic: "Our view is more comprehensive than cyber alone"
Vladimir Cibic has worked at KPN for over a quarter of a century in a wide variety of roles and was recently nominated for the 2025 CISO of the Year Award.

CISO of the Year Award special with Martin de Vries
In this episode, we talk to 2025 CISO of the Year Nominee Martin de Vries, CISO at Eindhoven Technical University (TU/e).

Martin de Vries: "No competition on security"
Martin de Vries has been the CISO at Eindhoven University of Technology since spring 2021. He was recently nominated for the 2025 CISO of the Year Award.

APT29 malware targets EU diplomats
Russian state-sponsored cyber-espionage group APT29, also known as Midnight Blizzard or Cozy Bear, has been linked to a new and sophisticated phishing campaign targeting Western diplomats.



